Amazon Web Services provides its customers with the broadest suite of networking services such as Amazon Virtual Private Cloud (VPC). That allows clients to obtain the best possible reliability, security, and performance for running applications in the cloud environment.
Today, we will learn about AWS Networking in detail, including:
- Describing the fundamentals of networking;
- Analyzing how public and private networking resources differ;
- Explaining a virtual private gateway;
- Considering the advantages of AWS Direct Connect;
- Defining the existing layers of security.
Connectivity to AWS
Millions of companies around the world utilize the available AWS services. Also, these numerous clients create required AWS resources like Amazon EC2 instances. If such resources have no appropriate boundaries, the network traffic can flow between them with no restrictions.
Amazon VPC
Amazon VPC is a networking service used for establishing boundaries around the organization’s AWS resources. Actually, it serves as a private network in AWS that allows provisioning a relevant isolated section within the AWS cloud. This section is called a subnet. With subnets, you may launch and group resources like Elastic Load Balancers (ELBs) or EC2 instances in a defined virtual network. After all, subnets and current networking rules help control whether your resources are in public or private availability.
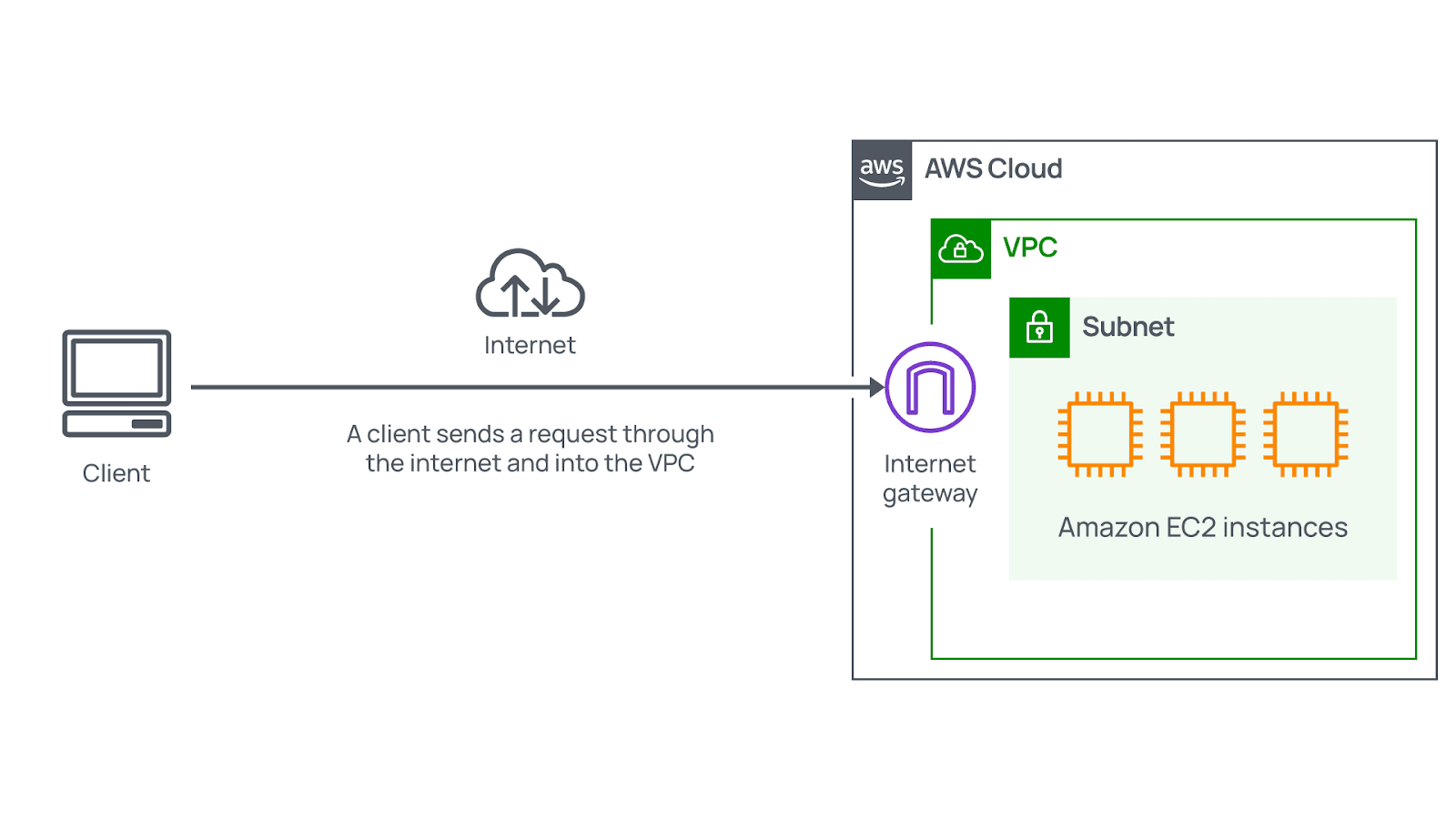
Internet gateway
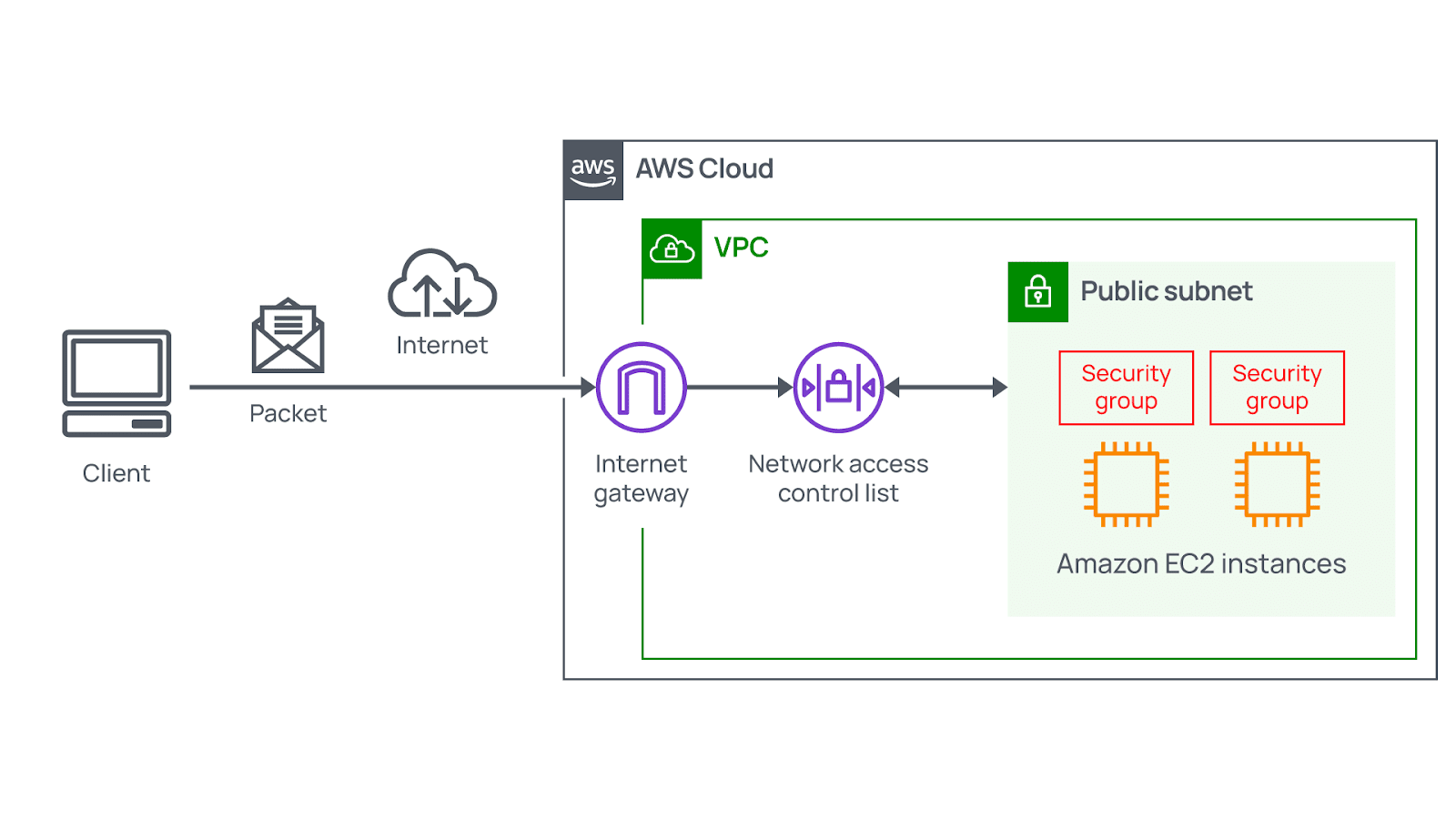
Your organization can use several critical approaches to controlling the traffic that flows into your Virtual Private Cloud. For some VPCs, you may deal with internet-facing resources. Such resources, including public websites, should be reachable by all internet users. Thus, you need to provide traffic from the public internet with the opportunity to get into and out of a relevant VPC. Attaching an internet gateway (IGW) to this VPC is the best way to do that.
It means that an internet gateway serves as the appropriate connection between the public internet and your VPC. Without it, accessing the available resources is impossible.
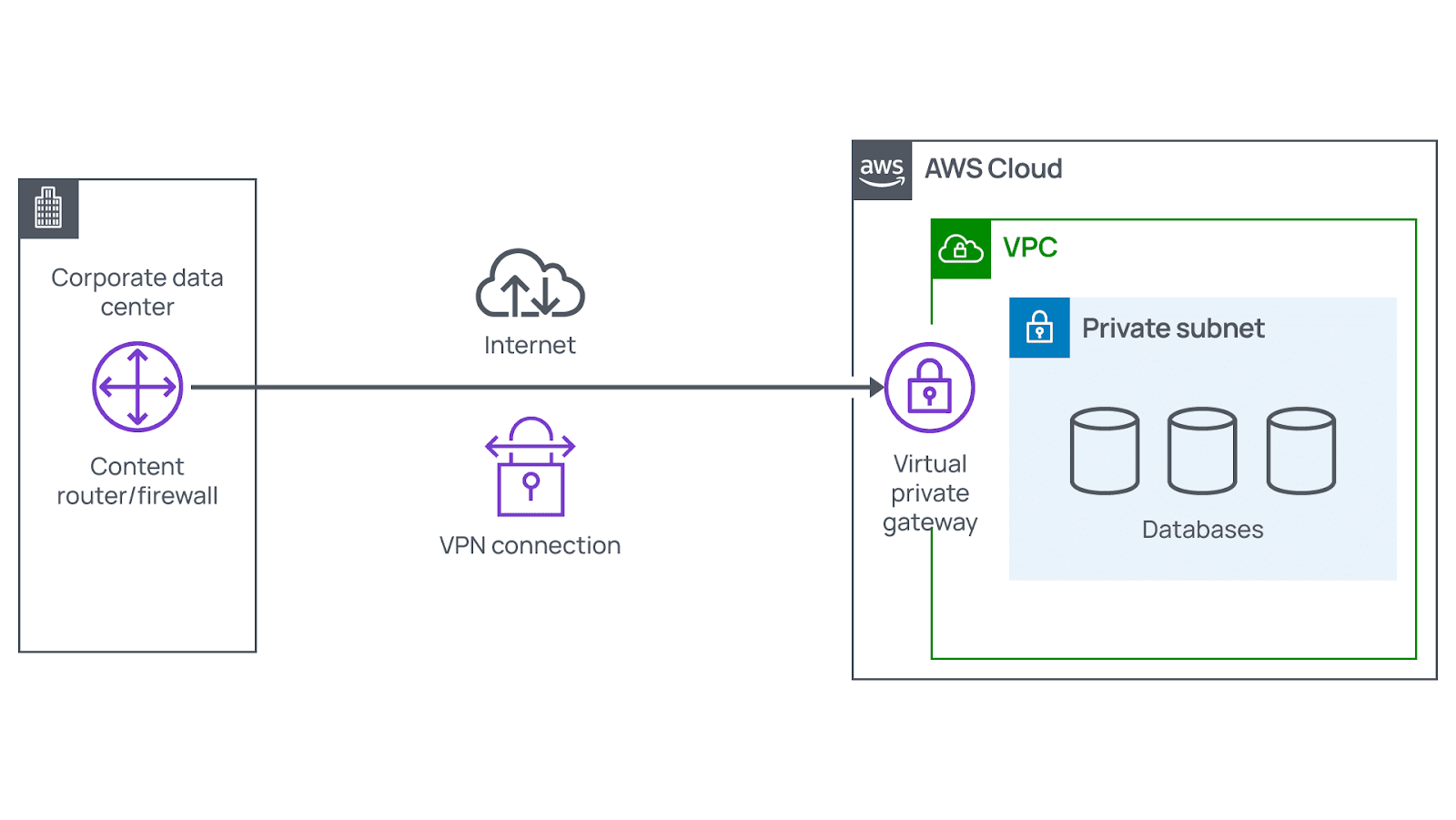
Virtual private gateway
In some scenarios, your organization can have resources reachable only for authorized users who log into your private network. Among these resources are internal services such as HR apps or backend databases. In this case, your business does not want to have them reachable by anyone publicly. Thus, there is no need to attach an internet gateway to your VPC. Instead, using a virtual private gateway is the best approach to accessing private resources.
A virtual private gateway allows users in when they come only from the approved network. It enables you to build a virtual private network (VPN) connection between the company’s VPC and a relevant private network. Among the most common examples of a private network are on-premises information centers and internal corporate networks. Although VPN connections depend on a traditional internet connection, they provide excellent privacy and encryption. That helps ensure the lowest possible latency, along with the highest possible security.
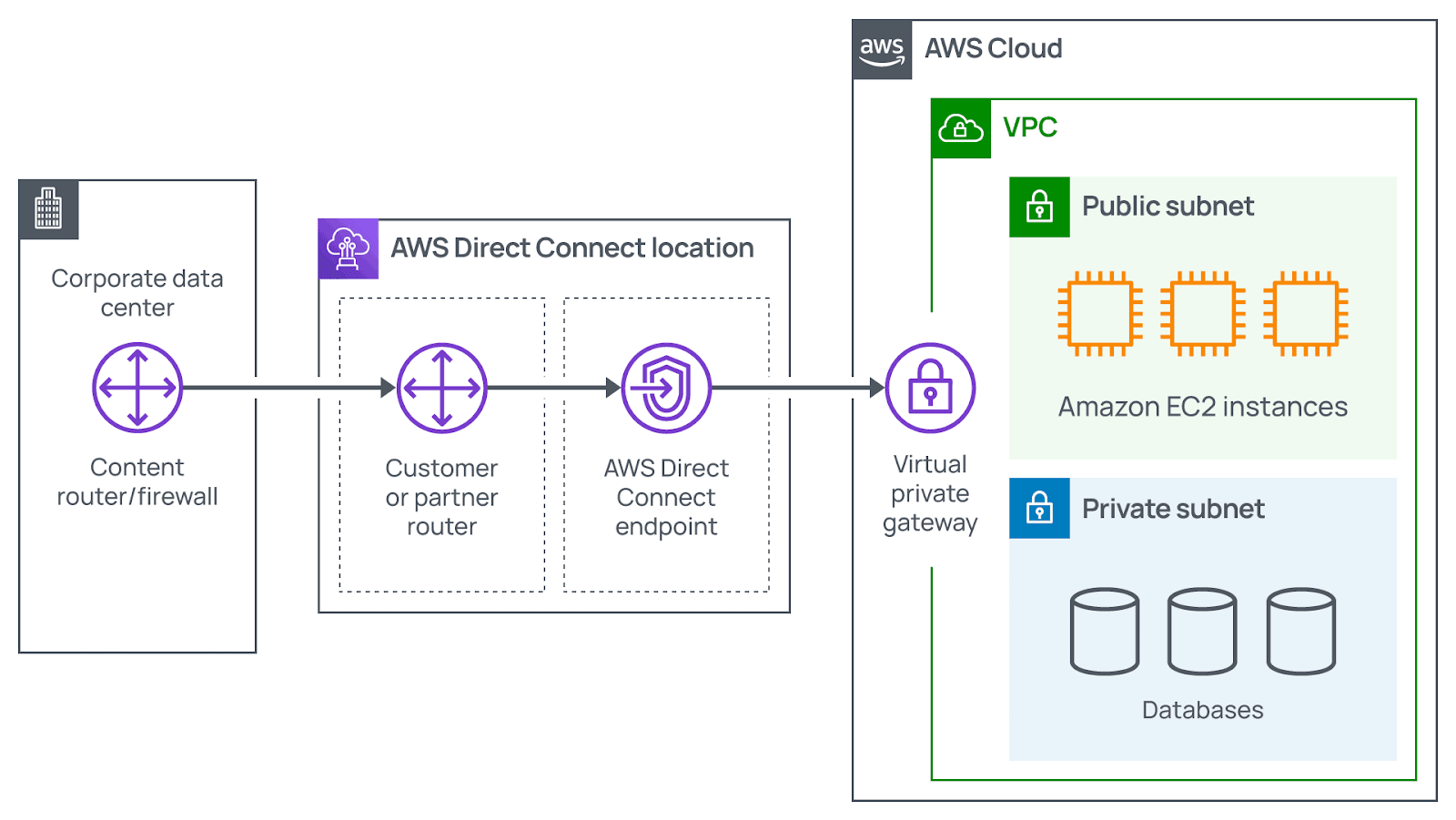
AWS Direct Connect
AWS Direct Connect is a critical service that allows establishing a connection between a Virtual Private Cloud and your data center. This particular connection is private, dedicated, and fiber, and it helps customers reduce their network costs. Besides, it promotes an increase in the amount of bandwidth traveling through their network.
Clients should cooperate with a relevant Direct Connect partner in their area for establishing the required connection. It involves providing a physical line connecting your network with a VPC. Thus, AWS Direct Connect allows meeting the existing regulatory and compliance requirements and avoiding various potential bandwidth issues.
Ultimately, one VPC can have multiple kinds of gateways you attach for different types of resources. They all reside in the same Virtual Private Cloud but various subnets.
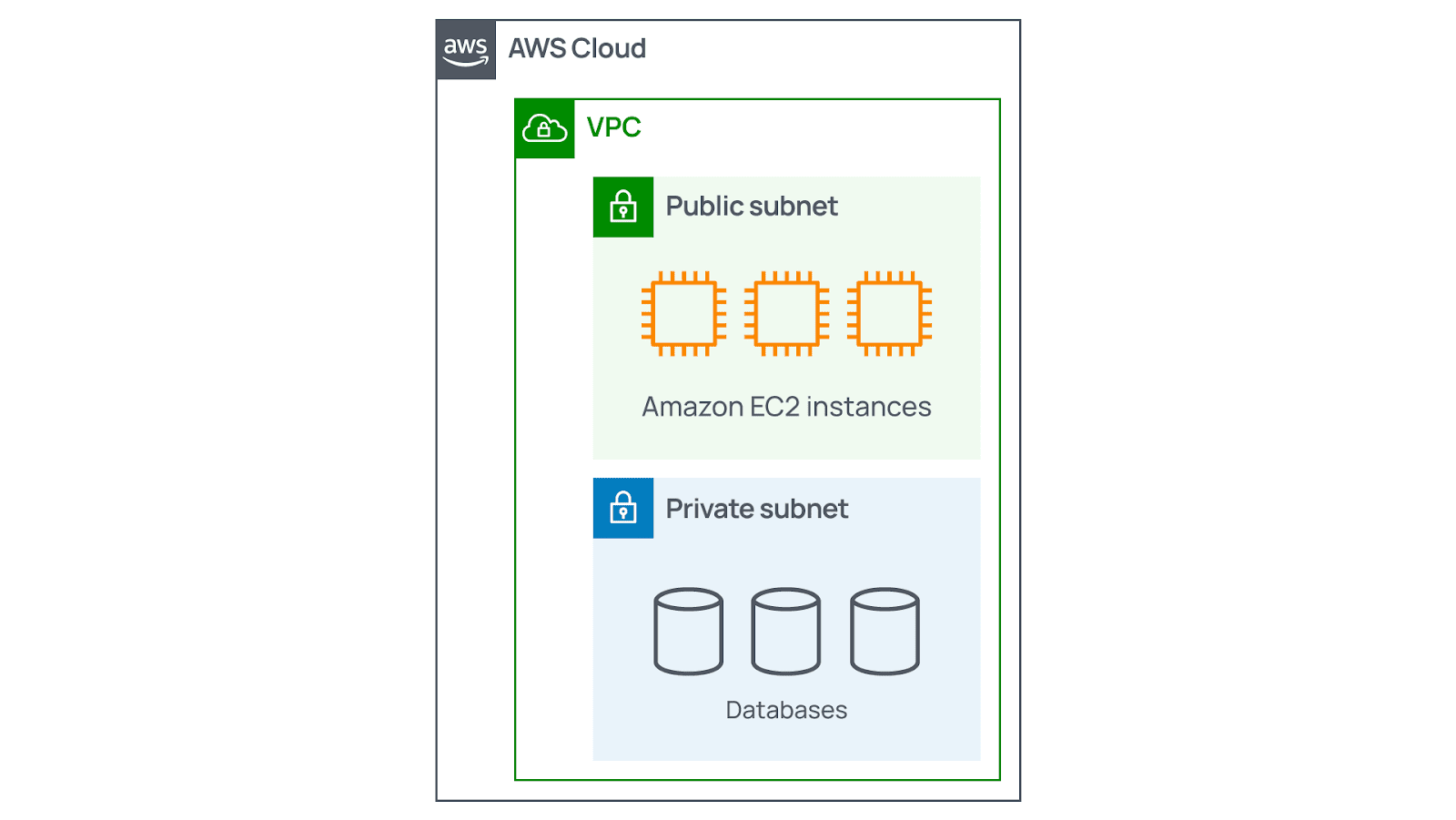
Subnets, network ACLs, and security groups
Having a gateway on your VPC allowing traffic to flow in and out is crucial. But this gateway is just one component of network security you should focus on when creating your IT strategy.
Amazon Web Services offers numerous tools covering all layers of security, including network hardening, app security, or user identity. That may also involve authentication and authorization, preventing DDoS attacks, information integrity, encryption, etc. Here, we will describe some critical aspects related to network hardening and analyze what happens within your VPC.
Subnets
Subnets serve as sections of a VPC where your organization can group resources depending on security or operational requirements. Also, the only technical goal to use them is to provide control over access to the existing gateways. There are two types of subnets: public and private.
- Public subnets include resources that should be reachable by the public, like eCommerce stores.
- Private subnets cover resources that should be reachable only via your private network. An example is a database that contains clients’ personal data and order history.
In a Virtual Private Cloud, subnets may maintain communication with each other. For instance, your company can have an application involving Amazon EC2 instances within a public subnet. And they can communicate with databases located in a relevant private subnet.
Network traffic in your VPC
When clients request information from applications the AWS Cloud hosts, such requests are sent as packets. Thus, a packet serves as a data unit sent using the internet or a network.
Packets flow into your VPC through a relevant internet gateway. Before entering into or exiting from subnets, they check for necessary permissions. Such permissions define who was the sender and how packets are trying to communicate with available resources within a subnet.
To check packet permissions for a subnet, you should utilize a specific VPC component called a network access control list (ACL).
Network ACLs
Network ACLs are considered the virtual firewalls that provide control of inbound and outbound traffic. They exist at the subnet level. Thus, an NACL allows approved traffic to continue its way. Meanwhile, potentially harmful traffic, including attempts to obtain control of your system using administrative requests, is blocked before touching its target.
All AWS accounts involve a default NACL. But when configuring your Virtual Private Cloud, you can also create custom ones. In the case of a default network ACL, your organization can add its own necessary rules for modifying it. On the other hand, using custom NACLs means denying all inbound and outbound traffic unless your company adds specific rules. Such rules must specify the traffic to allow. In addition, each network ACL has an explicit deny rule. It ensures that if packets match no other rules predicted by the list, they are denied.
Although network ACLs maintain the appropriate security, they cannot address all the existing network control problems. That is because NACLs only evaluate packets if they cross subnets boundaries. It means they do not evaluate if such packets can reach relevant EC2 instances. In some cases, your business may have different EC2 instances within the same subnet. However, these instances can deal with various rules like who can send messages to them. Therefore, you should also have network security at the instance level.
Stateless packet filtering
NACLs conduct stateless packet filtering. It means that they do not remember anything and check inbound and outbound packets crossing the subnet border. Let’s analyze the example of sending a relevant request out from your Amazon EC2 instance to the internet.
When a packet response for the request returns to the subnet, your network access control list remembers no previous request. The NACL should check the packet response against the existing list of rules. That allows determining whether to allow it or deny it. After entering your subnet, there must be an evaluation of the packet’s permissions regarding resources within a particular subnet. Among such resources are Amazon EC2 instances.
Finally, the VPC component that provides checking of packet permissions related to Amazon EC2 instances is called a security group.
Security groups
Security groups serve as virtual firewalls that control inbound and outbound traffic related to Amazon EC2 instances. When launching an EC2 instance, it automatically includes creating a security group. Basically, security groups deny all inbound traffic while allowing all outbound traffic. Your organization can also create custom rules for configuring what traffic types to allow or deny. For example, in terms of websites, your company may want to accept only web-based traffic or HTTPS. There is no need to accept the operating system and admin requests.
You may have numerous Amazon EC2 instances within your subnet. That allows associating these instances with the same group or using various security groups for each separate one.
But what is the main difference between security groups and network ACLs? The first ones are stateful, which means that they have some kind of memory referring to allowing inbound or outbound traffic. On the other hand, NACLs are stateless. They remember nothing and check all single packets crossing the subnet border, no matter what the circumstances are.
Stateful packet filtering
Security groups conduct stateful packet filtering. It means they remember decisions regarding incoming packets that were made previously. Let’s analyze the same example as in the case of stateless packet filtering.
When a packet response for the request returns to the instance, your security group tends to remember a previous request. Thus, security groups enable responses to proceed and pay no attention to the existing inbound rules.
The bottom line
Nowadays, AWS Networking is incredibly simplified and abstracted. That allows answering a critical question of who has permission for communicating with each other. Since your company knows how to answer this question, it can configure the network on AWS efficiently. Ultimately, the correct understanding of AWS Networking fundamentals enables your organizations to get started right now.
How AgileVision can help
As an official AWS Consulting Partner, AgileVision has helped companies of different types and sizes manage their AWS resources. Are you considering implementing new AWS Networking services to meet your specific business requirements or need advice on your current ones?
Need help with your cloud architecture?
Schedule a Free Consultation




